(A flaw in the design of this system was fixed and posted about here.)
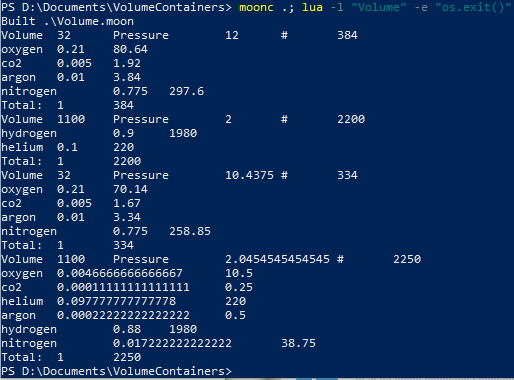
One of my game ideas involves constructing 2D spaceships, and the concept of a simplified system for storing fuel, oxygen, water – really any kind of fluid mixture – in storage tanks. Along with this, it allows simulating breaches between containers, hard vacuum, and the pressurized areas of the ship itself!
{ -- a rough approximation of Earth's atmosphere
pressure: 1
volume: 4.2e12 -- 4.2 billion km^3
contents: {
nitrogen: 0.775
oxygen: 0.21
argon: 0.01
co2: 0.005
}
}
{ -- hard vacuum
pressure: 0
volume: math.huge -- infinity
-- the contents table will end up containing negative infinity of anything that leaks into the vacuum
}It all comes down to storing a total pressure and volume per container, and a table of contents as percentages of the total mixture. The total amount of mass in the system can be easily calculated (volume * pressure), as can the amount of any item in the system ( volume * pressure * percent).
Breaches are stored as a reference in the container with a higher pressure, and a size value is added to the container with lower pressure (representing the size of the hole between them).
Limitations
- Everything has the same density and mixes evenly.
- There are no states of matter, everything is treated as a gas.
- Attempting to directly modify the amount of a fluid is prone to floating-point errors it seems, while mixing containers via the breach mechanic is working as expected.
The code was written in MoonScript / Lua and is available here.

